Phishing
Need to report a phishing email?
Use the “Report” button on Outlook or forward any suspicious messages to infosec@uc.edu for further review.
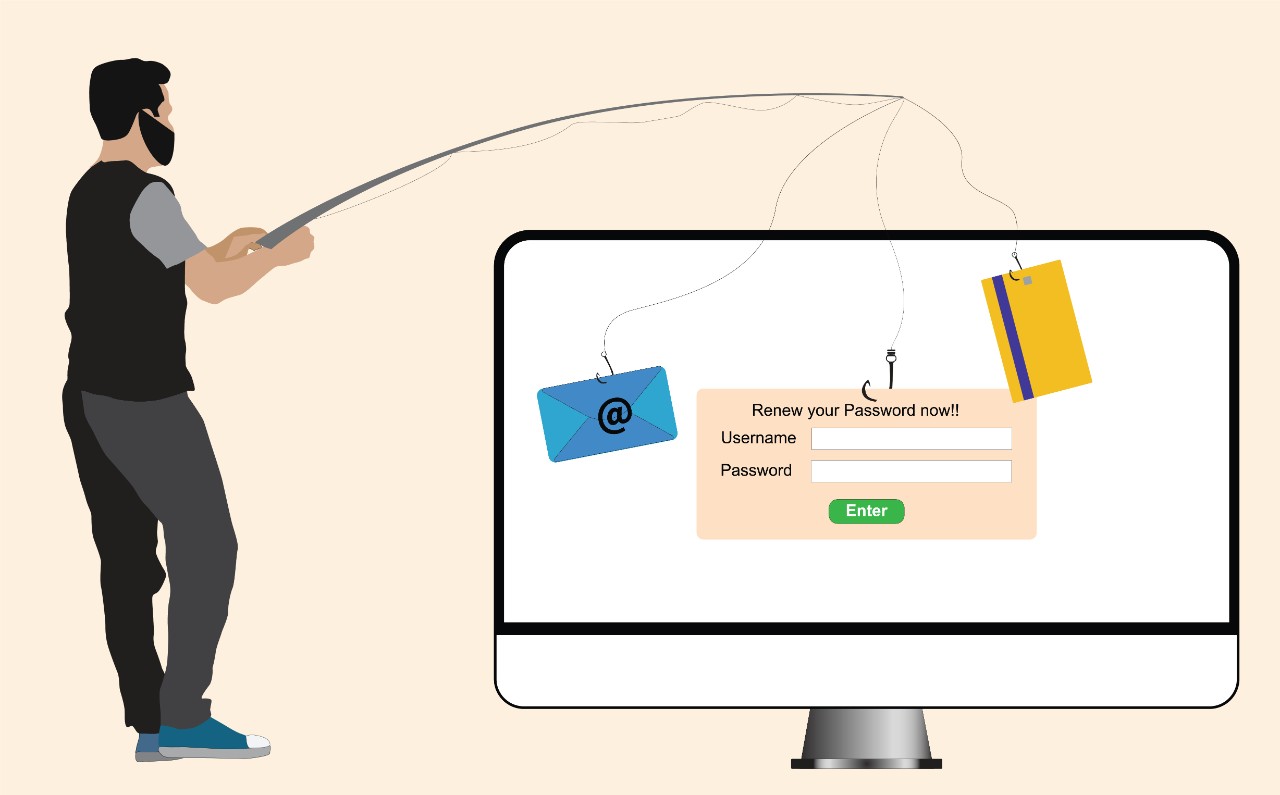
Phishing is a deceptive social engineering technique used by cybercriminals to trick you into divulging sensitive information such as usernames, passwords, social security numbers, and bank details. This method typically involves sending emails, texts, or messages that mimic legitimate communications to induce urgent actions like clicking on a link, opening an attachment, or verifying account details. These actions can lead to unauthorized access to personal and financial information.
For University of Cincinnati community members seeking further assistance or to report suspicious activities, please contact the Office of Information Security directly. Remember, the university will never request your username and password via email.
Being aware of these red flags can make all the difference in protecting your personal information. Stay vigilant, double-check details, and when in doubt, reach out to official channels for verification. Secure yourself now and avoid the headache of a compromise later!
- Generic salutations instead of personalized greetings.
- Urgent language that pressures you for immediate action.
- Links that appear legitimate but direct you elsewhere when clicked.
- Vague or irrelevant email subject lines.
- Lack of a detailed signature.
- Requests for sensitive information such as usernames or passwords.
- Presence of misspellings, grammatical errors, or inconsistent information.
- Be cautious with unsolicited emails or messages.
- Refrain from clicking on links or downloading attachments from unknown sources.
- Verify the security of websites by looking for "https://" in the URL and secure icons like a lock.
- Always type known URLs directly into the address bar rather than following links.
- Familiarize yourself with the domain names and visual cues of trusted sites, such as custom images or logos used during secure logins.
- Delay actions since phishing sites are typically short-lived.
- Verify the legitimacy of suspicious communications by contacting the organization directly.
- Utilize anti-phishing and anti-spyware tools, along with up-to-date antivirus software.
- Stay informed about current phishing tactics and consider securing your web browser based on recommendations from trusted cybersecurity sources.
Smishing
Text message (SMS) Phishing, also known as Smishing, targets you through mobile text messages. These messages often solicit sensitive data such as passwords or personal information by prompting actions like visiting a malicious link, sending money, or taking further action like making a phone call leading to fraudulent activity.
Smishing messages may mimic communications from banks or postal services to solicit personal or financial information. In university contexts, these messages might appear to come from high-ranking officials like the Chancellor, requesting purchases or personal data.
Quishing
Quishing, short for "QR code phishing," is a type of phishing attack where cybercriminals use QR codes to deceive victims into providing sensitive information or downloading malicious software. With the increasing popularity and convenience of QR codes, quishing has become a novel and effective method for attackers to exploit unsuspecting users.
This type of attack leverages the trust and ease of use associated with QR codes, making it a potent tool for cybercriminals. Be careful and verify by hovering over the QR code for URL.
Vishing
Vishing is a phishing attack that uses voice calls or text messages to trick users into divulging sensitive information.
Whaling
Whaling, also known as CEO fraud or executive phishing, involves attackers masquerading as high-ranking officials such as CEOs, CFOs, or other senior executives. These attackers carefully research their targets and craft convincing emails or messages that appear to come from a trusted source within the organization. The goal is often to trick the recipient into disclosing sensitive information, transferring funds, or downloading malware.
Spear Phishing
While phishing is a broad term for cyberattacks via email, SMS, or phone, targeted attacks are called spear phishing. These highly personalized attacks target specific individuals or companies, often through emails that appear legitimate to the recipient. Spear phishing aims to steal sensitive information like login credentials or credit card details, and can also infect devices with malware. Attackers, including government-sponsored hackers and individual cybercriminals, use social engineering to craft convincing messages.
Social engineering is the tactic of manipulating, influencing, or deceiving a victim in order to gain control over a computer system, or to steal personal and financial information. It uses psychological manipulation to trick users into making security mistakes or giving away sensitive information.The use of social engineering makes spear phishing more successful than standard phishing.
Traditional spear phishing defenses are often insufficient due to the sophistication of these attacks, making them hard to detect. A single mistake can have severe consequences for individuals, governments, businesses, or non-profits. While spear phishing can't be completely eradicated, various measures can add layers of security to reduce their likelihood. Here are some tips to prevent this type of attack:
- Regularly check for suspicious emails, especially those requesting password changes or containing suspicious links.
- Use a VPN to protect and encrypt online activity.
- Utilize anti-virus software to scan emails for malicious attachments, links, or downloads.
- Verify the source of emails and check URLs to avoid malicious links.
- Visit organizations’ websites directly instead of clicking email links.
- Keep all software updated with the latest security patches.
- Limit personal details shared online and adjust social media privacy settings.
- Use a password manager and create complex, unique passwords, changing them regularly.
- Enable multi-factor or biometric authentication where possible.
- Verify suspicious emails by contacting the sender directly.
Need IT Help?
- Get how-to instructions in the IT Knowledge Base.
- Submit a ticket.
- Or, call the IT Service Desk.
- From a personal phone, dial 513-556-HELP (4357) or 866-397-3382; select option 2.
- From a university phone on campus, dial 6-HELP (4357); select option 2.
- From a personal phone, dial 513-556-HELP (4357) or 866-397-3382; select option 2.